CCNP350-401学习笔记(1-50题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.17)https://blog.csdn.net/shuyan1115/article/details/129088574?spm=1001.2014.3001.5502CCNP350-401学习笔记(51-100题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.18)
https://blog.csdn.net/shuyan1115/article/details/129092241?spm=1001.2014.3001.5502CCNP350-401学习笔记(101-150题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.18)
https://blog.csdn.net/shuyan1115/article/details/129098277?spm=1001.2014.3001.5502CCNP350-401学习笔记(151-200题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.19)
https://blog.csdn.net/shuyan1115/article/details/129104174?spm=1001.2014.3001.5502CCNP350-401学习笔记(201-250题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.20)
https://blog.csdn.net/shuyan1115/article/details/129117806?spm=1001.2014.3001.5502CCNP350-401学习笔记(251-300题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.20)
https://blog.csdn.net/shuyan1115/article/details/129121130?spm=1001.2014.3001.5502CCNP350-401学习笔记(301-350题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.20)
https://blog.csdn.net/shuyan1115/article/details/129127643?spm=1001.2014.3001.5502CCNP350-401学习笔记(351-400题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.21)
https://blog.csdn.net/shuyan1115/article/details/129135454?spm=1001.2014.3001.5502CCNP350-401学习笔记(401-450题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2022.2.21)
https://blog.csdn.net/shuyan1115/article/details/129136750?spm=1001.2014.3001.5502CCNP350-401学习笔记(451-500题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.22)
https://blog.csdn.net/shuyan1115/article/details/129159127?spm=1001.2014.3001.5502CCNP350-401学习笔记(501-550题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.22)
https://blog.csdn.net/shuyan1115/article/details/129159898?spm=1001.2014.3001.5502CCNP350-401学习笔记(551-600题)_殊彦_sy的博客-CSDN博客CCNP350-401学习笔记(2023.2.22)
https://blog.csdn.net/shuyan1115/article/details/129161397?spm=1001.2014.3001.5502
1、Which component handles the orchestration plane of the Cisco SD-WAN?
A. vBond
B. vSmart
C. vManage
D. vEdge
2、What is a Type 1 hypervisor?
A. runs directly on a physical server and depends on a previously installed operating system
B. runs directly on a physical server and Includes its own operating system
C. runs on a virtual server and depends on an already installed operating system
D. runs on a virtual server and includes its own operating system
3、Which two LISP infrastructure elements are needed to support LISP to non-LISP internetworking? (Choose two.)
A. PETR
B. PITR
C. MR
D. MS
E. ALT
4、
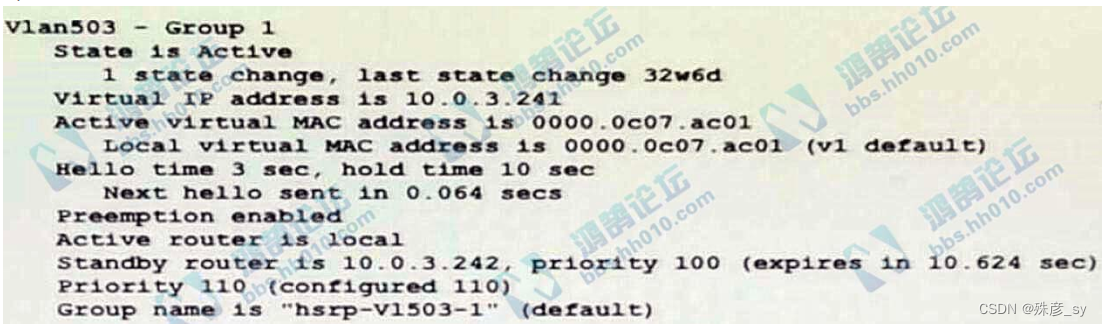
Refer to the exhibit. Which two facts does the device output confirm? (Choose two.)
A. The device's HSRP group uses the virtual IP address 10.0.3.242
B. The device is configured with the default HSRP priority.
C. The standby device is configured with the default HSRP priority.
D. The device is using the default HSRP hello timer.
E. The device sends unicast messages to its peers
5、Which two statements about VRF-lite are true? (Choose two)
A. It can support multiple customers on a single switch
B. It supports most routing protocols, including EIGRP, ISIS, and OSPF
C. It should be used when a customer’s router is connected to an ISP over OSPF
D. It can increase the packet switching rate
E. It supports MPLS-VRF label exchange and labeled packets
6、Which statement about agent-based versus agentless configuration management tools is true?
A. Agentless tools use proxy nodes to interface with slave nodes.
B. Agentless tools require no messaging systems between master and slaves.
C. Agent-based tools do not require a high-level language interpreter such as Python or Ruby on slave nodes.
D. Agent-based tools do not require installation of additional software packages on the slave nodes
7、Which two namespaces does the LISP network architecture and protocol use? (Choose two)
A. TLOC
B. RLOC
C. DNS
D. VTEP
E. EID
8、What is the fact about Cisco EAP-FAST?
A. It requires a client certificate.
B. It is an IETF standard.
C. It does not require a RADIUS server certificate.
D. It operates in transparent mode
9、
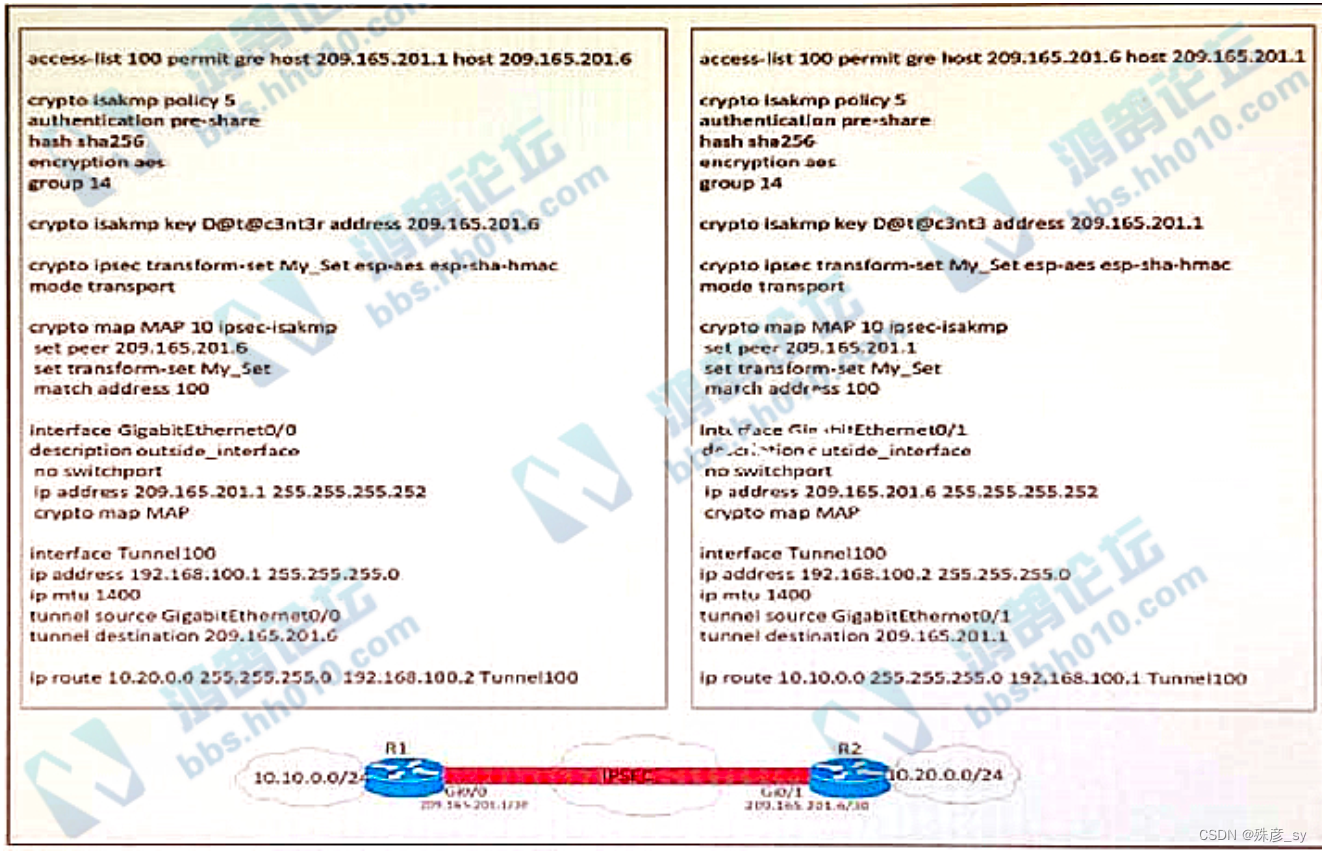
Refer to the exhibit. A network engineer must simplify the IPsec configuration by enabling IPsec over GRE
using IPsec profiles. Which two configuration changes accomplish this? (Choose two).
A. Remove the crypto map and modify the ACL to allow traffc between 10.10.0.0/24 to 10.20.0.0/24.
B. Create an IPsec profile, associate the transform-set ACL, and apply the profile to the tunnel interface.
C. Apply the crypto map to the tunnel interface and change the tunnel mode to tunnel mode ipsec ipv4
D. Remove all configuration related to crypto map from R1 and R2 and eliminate the ACL
E. Create an IPsec profile, associate the transform-set, and apply the profile to the tunnel interface.
10、 A GRE tunnel is down with the error message %TUN-5-RECURDOWN:
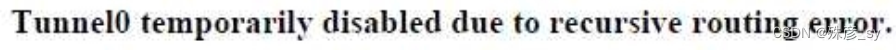
Which two options describe possible causes of the error? (Choose two.)
A. Incorrect destination IP addresses are configured on the tunnel.
B. There is link flapping on the tunnel
C. There is instability in the network due to route flapping
D. The tunnel mode and tunnel IP address are misconfigured
E. The tunnel destination is being routed out of the tunnel interface
11、 Which router is elected the IGMP Querier when more than one router is in the same LAN segment?
A. The router with the longest uptime
B. The router with the shortest uptime.
C. The router with the highest IP address
D. The router with the lowest IP address
12、How do agent-based versus agentless configuration management tools compare?
A. Agent-based tools do not require a high-level language interpreter such as Python or Ruby on slave nodes
B. Agentless tools require no messaging systems between master and slaves.
C. Agent-based tools do not require instaltation of additional software packages on the slave nodes
D. Agentless tools use proxy nodes to interface with slave nodes
13、In a traditional 3 tier topology, an engineer must explicitly configure a switch as the root bridge and exclude it from any further election process for the spanningtree domain. Which action accomplishes this task?
A. Configure the spanning-tree priority to 32768
B. Configure root guard and portfast on all access switch ports
C. Configure BPDU guard in all switch-to-switch connections
D. Configure the spanning-tree priority equal to 0
14、Which two statements about EIGRP load balancing are true? (Choose two)
A. Cisco Express Forwarding is required to load-balance across interfaces
B. A path can be used for load balancing only if it is a feasible successor
C. EIGRP supports unequal-cost paths by default
D. Any path in the EIGRP topology table can be used for unequal-cost load balancing
E. EIGRP supports 6 unequal-cost paths
15、What does the LAP send when multiple WLCs respond to the CISCO_CAPWAPCONTROLLER.localdomain hostname during the CAPWAP discovery and join process?
A. broadcast discover request
B. join request to all the WLCs
C. unicast discovery request to each WLC
D. Unicast discovery request to the first WLC that resolves the domain name
16、Refer to the exhibit. An engineer must establish eBGP peering between router R3 and router R4. Both routers should use their loopback interfaces as the BGP router ID.
Which configuration set accomplishes this task?
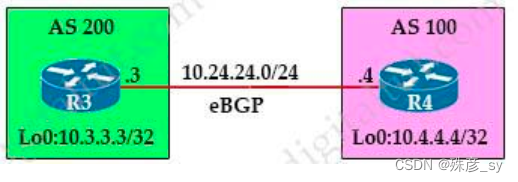
A. R3(config)#router bgp 200
R3(config-router)#neighbor 10.24.24.4 remote-as 100
R3(config-router)#bgp router-id 10.3.3.3
R4(config)#router bgp 100
R4(config-router)#neighbor 10.24.24.3 remote-as 200
R4(config-router)#bgp router-id 10.4.4.4
B. R3(config)#router bgp 200
R3(config-router)#neighbor 10.4.4.4 remote-as 100
R3(config-router)#neighbor 10.4.4.4 update-source loopback0
R4(config)#router bgp 100
R4(config-router)#neighbor 10.3.3.3 remote-as 200
R4(config-router)#neighbor 10.3.3.3 update-source loopback0
C. R3(config)#router bgp 200
R3(config-router)#neighbor 10.24.24.4 remote-as 100
R3(config-router)#neighbor 10.24.24.4 update-source loopback0
R4(config)#router bgp 100
R4(config-router)#neighbor 10.24.24.3 remote-as 200
R4(config-router)#neighbor 10.24.24.3 update-source loopback0
17、
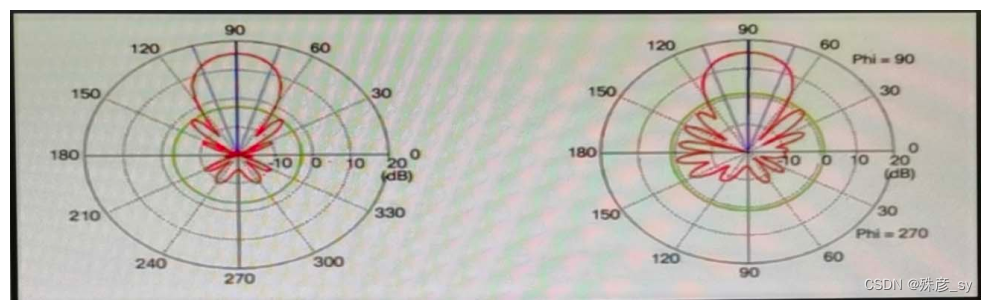
Refer to the exhibit. Which type of antenna is shown on the radiation patterns?
A. Yagi
B. dipole
C. patch
D. omnidirectional
18、Which behavior can be expected when the HSRP version is changed from 1 to 2?
A. No changes occur because the standby router is upgraded before the active router.
B. No changes occur because version 1 and 2 use the same virtual MAC OUI.
C. Each HSRP group reinitializes because the virtual MAC address has changed.
D. Each HSRP group reinitializes because the multicast address has changed.
19、
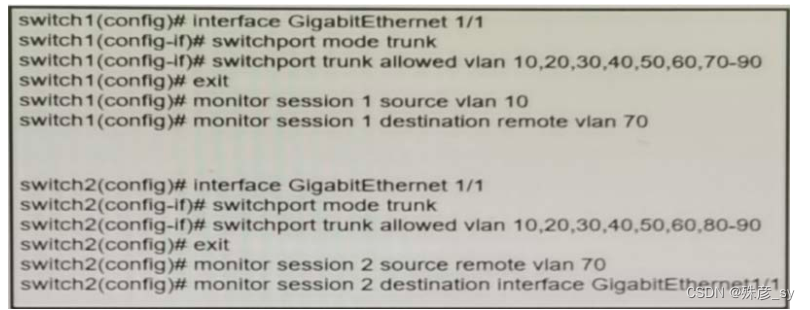
Refer to the exhibit A network administrator confiqured RSPAN to troubleshoot an issue between switch1 and switch2. The switches are connected using interface GigabitEthernet 1/1. An external packet capture device is connected to swich2 interface GigabitEthernet1/2. Which two commands must be added to complete this confiquration? (Choose two.)
A. switch2(config)# monitor session 2 destination vlan 10
B. switch1(config)# interface GigabitEthernet 1/1
switch1(confia-if# switchport mode access
switch1(config-if)# switchport access vlan 10
switch2(config)# interface GigabitEthernet 1/1
switch2(config-if)# switchport mode access
switch2(config-if)# switchport access vlan 10
C. switch2(config)# monitor session 1 source remote vlan 70
switch2(config)# monitor session 1 destination interface GigabitEthernet1/1
D. switch2(config-if)# switchport trunk allowed vlan 10,20,30,40,50,60,70-80
E. switch2(config)# monitor session 1 source remote vlan 70
switch2(confia)# monitor session 1 destination interface GigabitEthernet1/2
20、 What is the responsibility of a secondary WLC?
A. It enables Layer 2 and Layer 3 roaming between itself and the primary controller.
B. It shares the traffic load of the LAPs with the primary controller
C. It avoids congestion on the primary controller by sharing the registration load on the LAPs.
D. It registers the LAPs if the primary controller fails.
21、Which LISP infrastructure device provides connectivity between non-LISP sites and LISP sites by receiving non-LISP traffic with a LISP site destination?
A. PITR
B. map resolver
C. map server
D. PETR
22、A network administrator applies the following configuration to an IOS device.
aaa new-model
aaa authentication login default local group tacacs+
What is the process of password checks when a login attempt is made to the device?
A. A TACACS+ server is checked first. If that check fail, a database is checked
B. A TACACS+ server is checked first. If that check fail, a RADIUS server is checked. If that check fail, a
local database is checked
C. A local database is checked first. If that fails, a TACACS+server is checked, if that check fails, a RADIUS server is checked
D. A local database is checked first. If that check fails, a TACACS+server is checked
23、Which two statements about IP SLA are true? (Choose two)
A. It uses NetFlow for passive traffic monitoring
B. It can measure MOS
C. The IP SLA responder is a component in the source Cisco device
D. It is Layer 2 transport-independent
E. It uses active traffic monitoring
F. SNMP access is not supported
24、which antenna type should be used for a site-to-site wireless connection?
A. path
B. omnidirectional
C. dipole
D. Yagi
25、Refer to the exhibit.
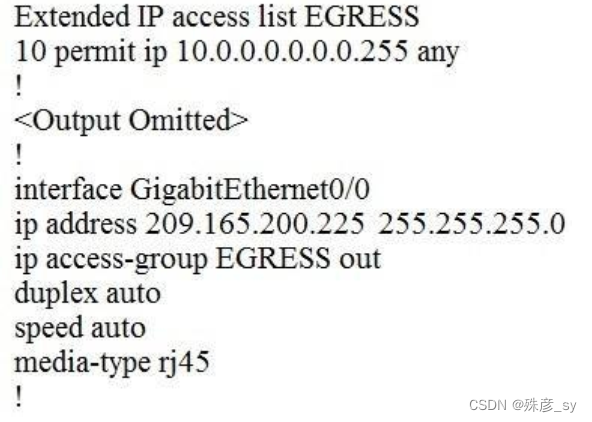
An engineer must block all traffic from a router to its directly connected subnet 209.165.200.0/24. The engineer applies access control list EGRESS in the outbound direction on the GigabitEthernet0/0 interface of the router. However, the router can still ping hosts on the 209.165.200.0/24 subnet.
Which explanation of this behavior is true?
A. Access control lists that are applied outbound to a router interface do not affect traffic that is sourced from the router.
B. After an access control list is applied to an interface, that interface must be shut and no shut for the access control list to take effect.
C. Only standard access control lists can block traffic from a source IP address.
D. The access control list must contain an explicit deny to block traffic from the router.
26、A customer has several small branches and wants to deploy a Wi-Fi solution with local management using CAPWAP.
Which deployment model meets this requirement?
A. local mode
B. autonomous
C. SD-Access wireless
D. Mobility Express
27、Which two actions provide controlled Layer 2 network connectivity between virtual machines running on the same hypervisor? (Choose two.)
A. Use a virtual switch running as a separate virtual machine.
B. Use a virtual switch provided by the hypervisor
C. Use a single trunk link to an external Layer2 switch.
D. Use a single routed link to an external router on stick.
E. Use VXLAN fabric after installing VXLAN tunneling drivers on the virtual machines.
28、Refer to exhibit. What are two reasons for IP SLA tracking failure? (Choose two )
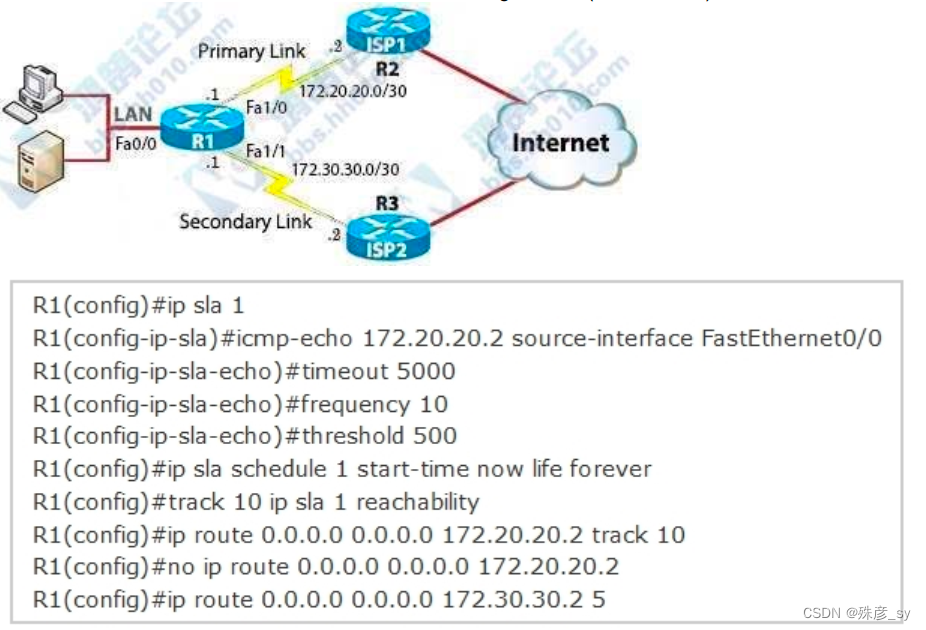
A. The source-interface is configured incorrectly
B. The destination must be 172.30.30.2 for icmp-echo
C. A route back to the R1 LAN network is missing in R2
D. The default route has wrong next hop IP address
E. The threshold value is wrong
29、In a Cisco SD- Access fabric, which control plane protocol is used for mapping and resolving endpoints?
A. DHCP
B. VXLAN
C. SXP
D. LISP
30、Which method should an engineer use to deal with a long-standing contention issue between any two VMs on the same host?
A. Adjust the resource reservation limits
B. Live migrate the VM to another host
C. Reset the VM
D. Reset the host
31、
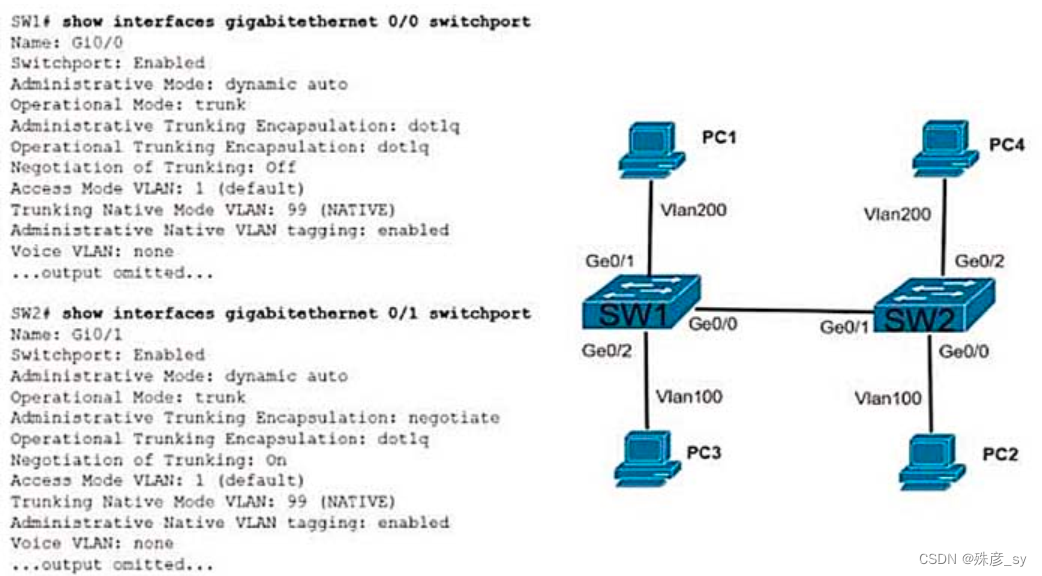
Refer to the exhibit.The connection between SW1 and SW2 is not operational.which two actions resolve the issue ?
A. configure switchport nonegotiate on SW1
B. configure switchport nonegotiate on SW2
C. configure switchport mode trunk on SW2
D. condigure switchport mode dynamic desirable on SW2
E. configure switchport mode access on SW2
32、What is a characteristic of a virtual machine?
A. It must be aware of other virtual machines, in order to allocate physical resource for
them
B. It is deployable without a hypervisor to host it
C. It must run the same operating system as its host
D. It relies on hypervisor to allocate computing resources for it